Preventing SQL Injection in PHP Tutorial
Introduction
In this tutorial, I will teach you how to Prevent SQL Injection in writing your PHP Queries for your current and future PHP Projects. This tutorial aims to give the IT/CS Students or those new to PHP Language a reference to learn for securing their database data in PHP. Here, I will be providing some snippets with a sample source code that demonstrates our topic for this tutorial.
What is SQL Injection?
An injection attack known as SQL Injection (SQLi) enables the execution of malicious SQL commands. These commands manage a database server that sits in front of a web application. SQL Injection flaws allow attackers to get around application security safeguards. The full content of a SQL database can be retrieved by getting past authentication and authorization of a web page or online application. They can also add, alter, and delete records in the database using SQL Injection.
How to Prevent SQL Injection in PHP?
To prevent SQL Injection in your PHP Project that uses MySQL Database. You must practice the following step for writing your PHP Code and MYSQL Queries.
- Validate and Sanitize Input Data
- Use a Prepared Statement
- Bind Query Parameters
- Execute the Queries
The above step can be achieved by using PDO and MySQLi.
Example
Below are the sample snippets for both vulnerable and prevents SQL Injection. You will see the sample result for both.
Database Schema and Data
Let's pretend that we have the following database schema and data in our database. The table is the user list of your web application which contains the user access.
Sample Form
Here is the sample login form for fetching and checking the user credential. I will only be using text type for the password input field just for demonstration purposes only for this tutorial.
Output
Sample Data
Use the "anything' or 'x' = 'x" as the username and password to the form and see the result for both PHP Queries execution of the snippets below.
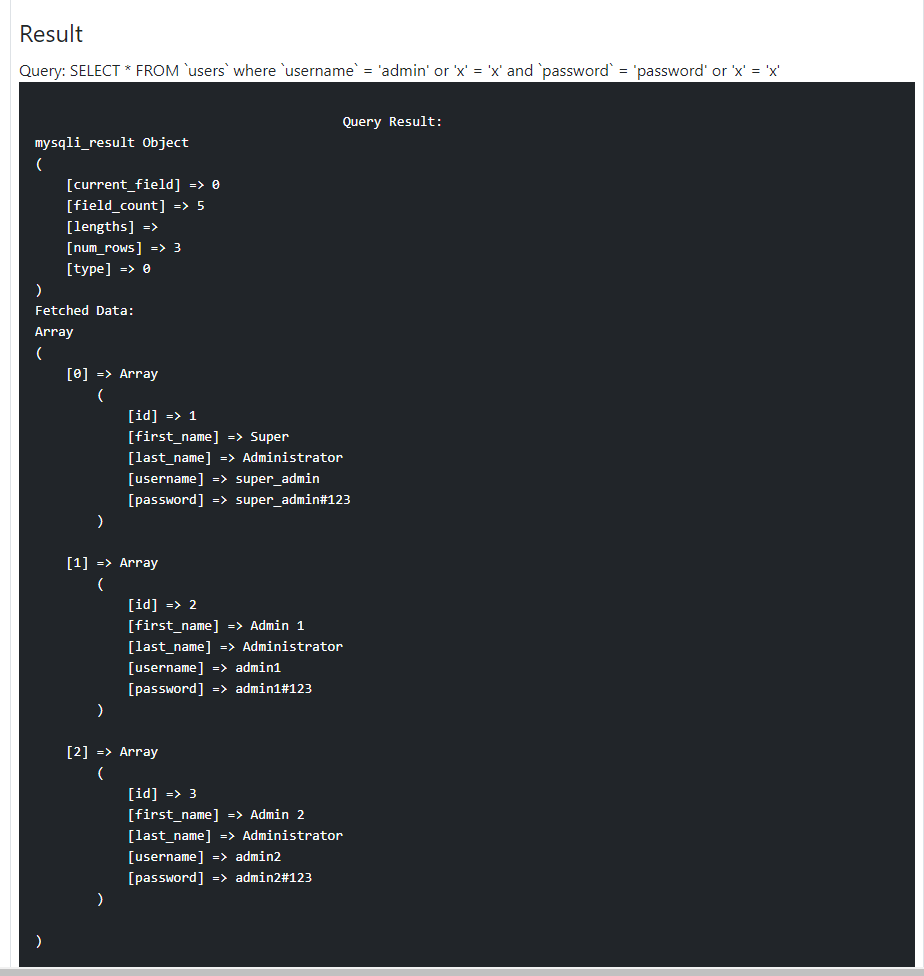
Sample Vulnerable PHP Script
The following PHP Code is an example of vulnerable to SQL Injection.
Output
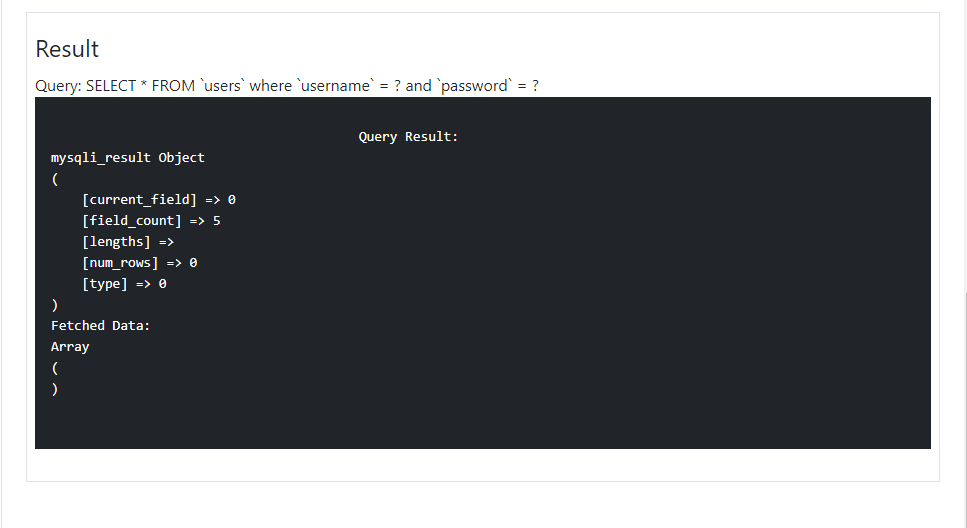
Sample PHP Script that Prevents SQL Injection
The following PHP script is an example of a PHP Query that prevents SQL Injections. The script below is using MySQLi Prepared statement and sanitizes input data.
Output
That's it! I also created and provided a simple web application that demonstrates How to Prevent SQL Injection in PHP. The download button is located below this article. Feel free to download and modify it.
That's the end of this tutorial. I hope this tutorial will help you learn to secure your PHP Projects. Explore more on this website for more Tutorials and Free Source Codes.
Happy Coding :)
Add new comment
- 666 views

